- About MAA
- Membership
- MAA Publications
- Periodicals
- Blogs
- MAA Book Series
- MAA Press (an imprint of the AMS)
- MAA Notes
- MAA Reviews
- Mathematical Communication
- Information for Libraries
- Author Resources
- Advertise with MAA
- Meetings
- Competitions
- Programs
- Communities
- MAA Sections
- SIGMAA
- MAA Connect
- Students
- MAA Awards
- Awards Booklets
- Writing Awards
- Teaching Awards
- Service Awards
- Research Awards
- Lecture Awards
- Putnam Competition Individual and Team Winners
- D. E. Shaw Group AMC 8 Awards & Certificates
- Maryam Mirzakhani AMC 10 A Awards & Certificates
- Two Sigma AMC 10 B Awards & Certificates
- Jane Street AMC 12 A Awards & Certificates
- Akamai AMC 12 B Awards & Certificates
- High School Teachers
- News
You are here
The Theorem that Won the War: Activities for Part 1.2 (Encryption)
Suggestion: The encryption activities are easier if they are done as group activities, with one person calling out the keyboard encryptions and the other the reflector encryptions.
For activities 1–4 in this section, we continue with the example from the previous page, for which the "Initial Setup" was as follows:
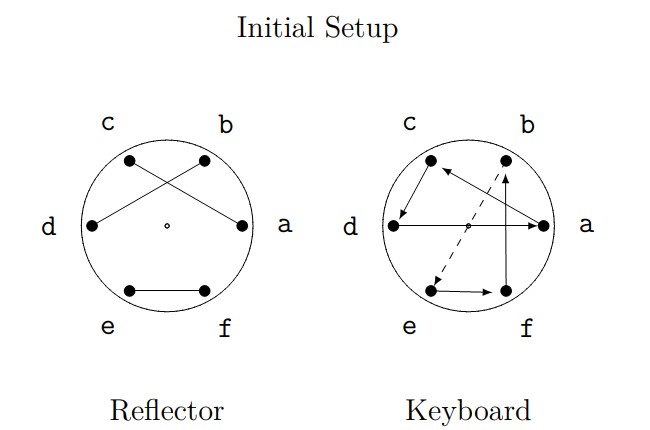
- Consider the initial setup shown above.
- Draw a rotor corresponding to the keyboard rotor.
- Explain why, when the current is moving right-to-left, we use the encryption \(a \rightarrow c\), but when the current is moving left-to-right, we use the backward encryption \(a \rightarrow d\).
- Express, in Cauchy two-line notation, the permutation used for the first; second; and third letters in the encryption of the message \(cab\) that we completed on the previous page using the initial setup shown above.
- Suppose we want to send the message \(cab \, bad\) using the initial setup shown above. Complete the encryption. Ignore the space, so that the \(b\) of \(bad\) will be the fourth letter that needs to be encrypted.
- An encryption system is not useful unless the recipients can decrypt the messages. Suppose you receive the encrypted message \(dbf\).
- “Reset” the paper Enigma to the initial setup shown above. Then encrypt \(dbf\). What do you notice?
- Continue on with the rest of your encrypted version of the message \(cab \, bad\). What happens?
- Notice that the initial placement of the rotors is arbitrary. Suppose the initial setup of the rotors is as shown below:
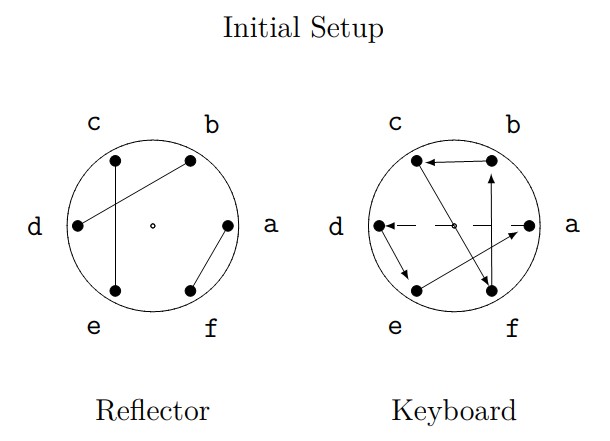
- Encrypt the word \(cab\) using this initial setup.
- Express, in Cauchy two-line notation, the encryption used for the first; second; and third letters.
- Now suppose your initial setup is:
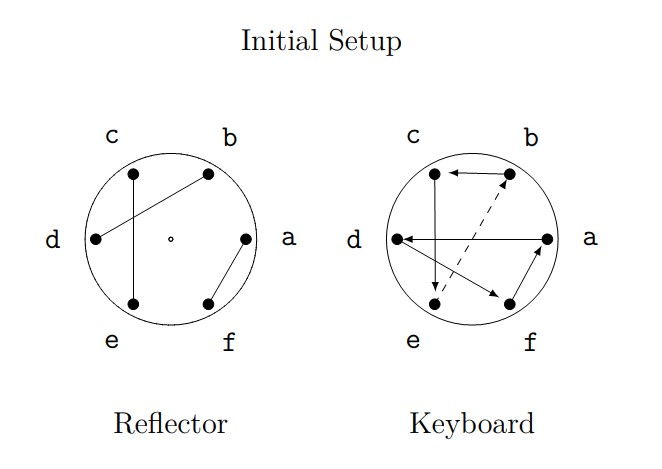
- Use this initial setup to encrypt the message: \(faded \, cab\).
- Verify that using the same initial setup will decrypt the message correctly.
- Explain why it is impossible for any rotor and reflector set to encrypt a letter as itself.
Jeff Suzuki (Brooklyn College), "The Theorem that Won the War: Activities for Part 1.2 (Encryption)," Convergence (October 2023)




